Enabling SSL with Spring Boot in real life
It is possible to enable SSL when running a Spring Boot application, without having to rely on a proxy like Nginx. However, the Spring Boot documentation on this subject is a bit scarce and I wanted to document the whole process.
In a previous article, I have described how to enable SSL in a Spring Boot application using self-signed certificates. I will now explain how to integrate this will real and secure certificates.
Disclaimer
For my example, I've used the (paying) services of DigiCert, which I use for the SSL of the Ontrack demonstration site.
Generating a certificate
You start by creating a CSR (Certificate Signing Request), for example using the DigiCert tool.
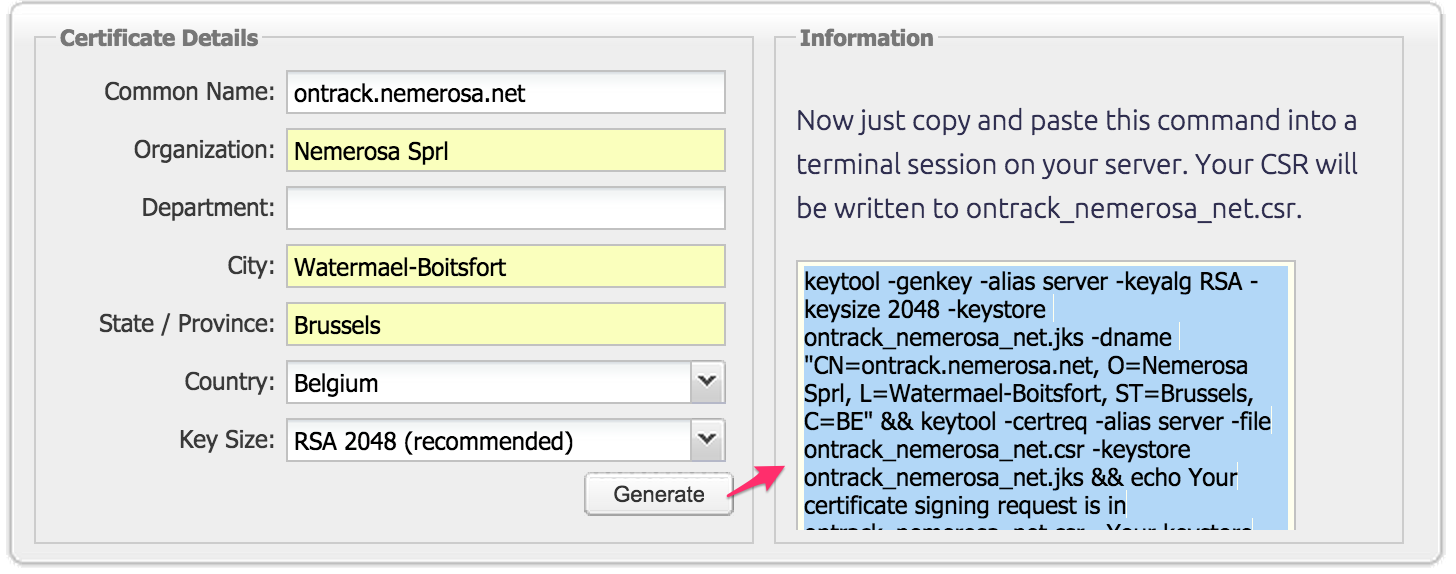
Enter the information and copy the generated command, for example:
keytool -genkey -alias server \
-keyalg RSA -keysize 2048 \
-keystore ontrack_nemerosa_net.jks \
-dname "CN=ontrack.nemerosa.net, O=Nemerosa Sprl, L=Watermael-Boitsfort, ST=Brussels, C=BE" &&
keytool -certreq -alias server \
-file ontrack_nemerosa_net.csr \
-keystore ontrack_nemerosa_net.jks &&
echo Your certificate signing request is in ontrack_nemerosa_net.csr. Your keystore file is ontrack_nemerosa_net.jks. Thanks for using the DigiCert keytool CSR helper.
You will be asked to choose a keystore password to protect your new keystore file. Then press RETURN to use the same password for the certificate's private key. Then you will be asked to type the keystore password once more to create the CSR file.
When ordering your certificate, you'll be asked for the content of the CSR:
-----BEGIN NEW CERTIFICATE REQUEST-----
MIIC6jCCAdICAQAwd...
-----END NEW CERTIFICATE REQUEST-----
If asked for a platform, enter Tomcat.
The validation of the CSR can take some time.
Once everything is in order, you receive a .p7b file, like ontrack_nemerosa_net.p7b.
Creating a keystore
See the DigiCert documentation for some additional details.
In the same directory than you initial .jks file, run the following command:
keytool -import -trustcacerts -alias server -file certs/ontrack_nemerosa_net.p7b -keystore ontrack_nemerosa_net.jks
You will be asked for the keystore password.
The keystore file (ontrack_nemerosa_net.jks in our example) is ready to be used.
Spring Boot configuration
The application properties, typically in an application.yml (see below for more details), must contain the following attributes:
server:
port: 443
ssl:
enabled: true
key-alias: server
key-store: "config/ontrack_nemerosa_net.jks"
key-store-password: "***"
Do not release this file in Git or anywhere else.
Keeping the configuration secret
Of course, you cannot release the configuration file, containing sensible information, into your SCM. Instead, we can use the Spring Boot capabilities to get its configuration from a hierarchy of sources.
In the Ontrack application, I have the following hierarchy:
config/application.properties- packaged with the application, and containing general settings, not dependent on the environmentapplication.properties- packaged with the application, generated at build time, containing information about the versionconfig/application.yml- stored in the SCM, deployed automatically on the server, in the working directory, containing environment specific information, but no secretconfig/application-prod.yml- not stored anywhere, containing secrets and maintained directly on the host (and no where else), in the working directory
In Ontrack, I'm using a prod Spring profile, which allows me to define a specific configuration file for this profile. When using no profile, you can always have a secret configuration file in application.yml, stored in the working directory.
See also my previous article for additional information about enabling SSL in Spring Boot.